First Class Info About How To Detect Hacking

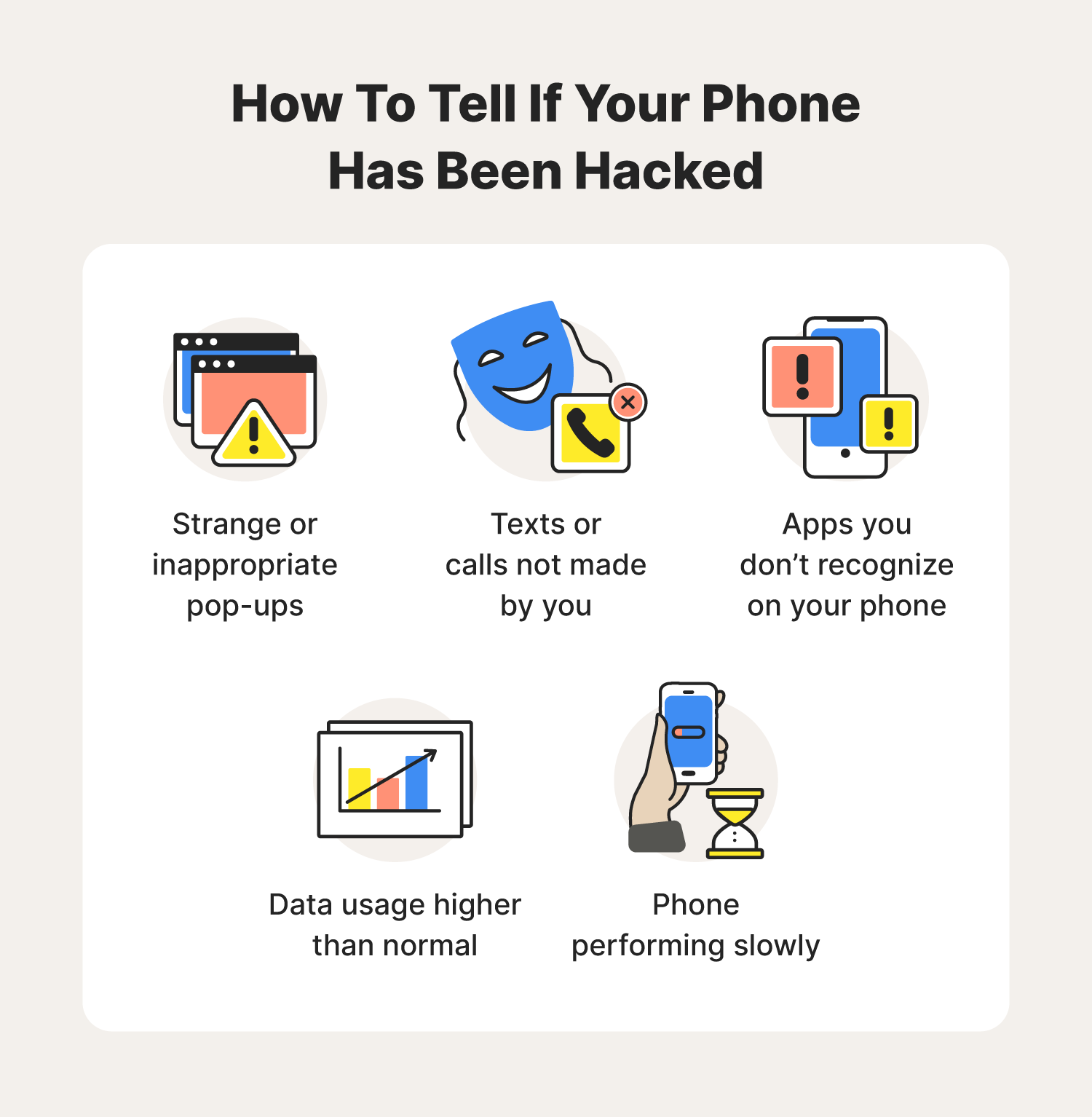
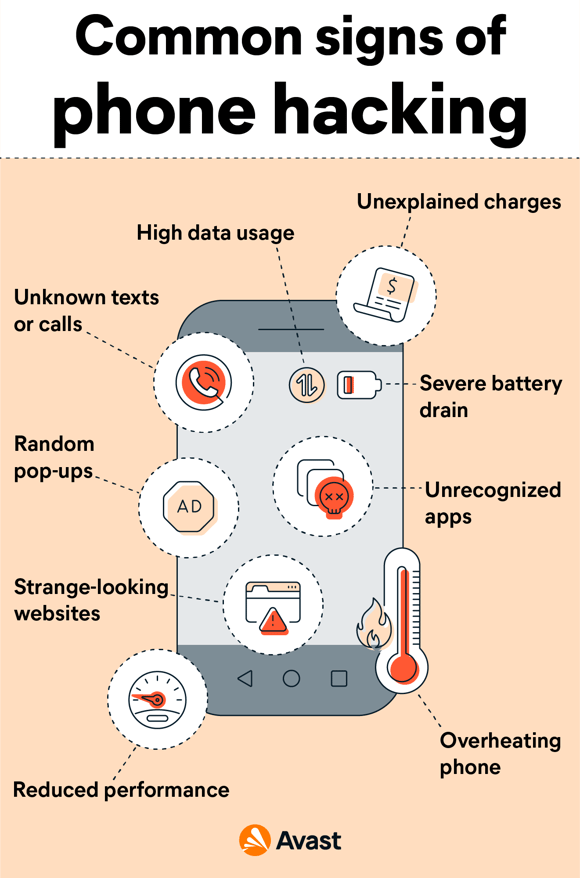
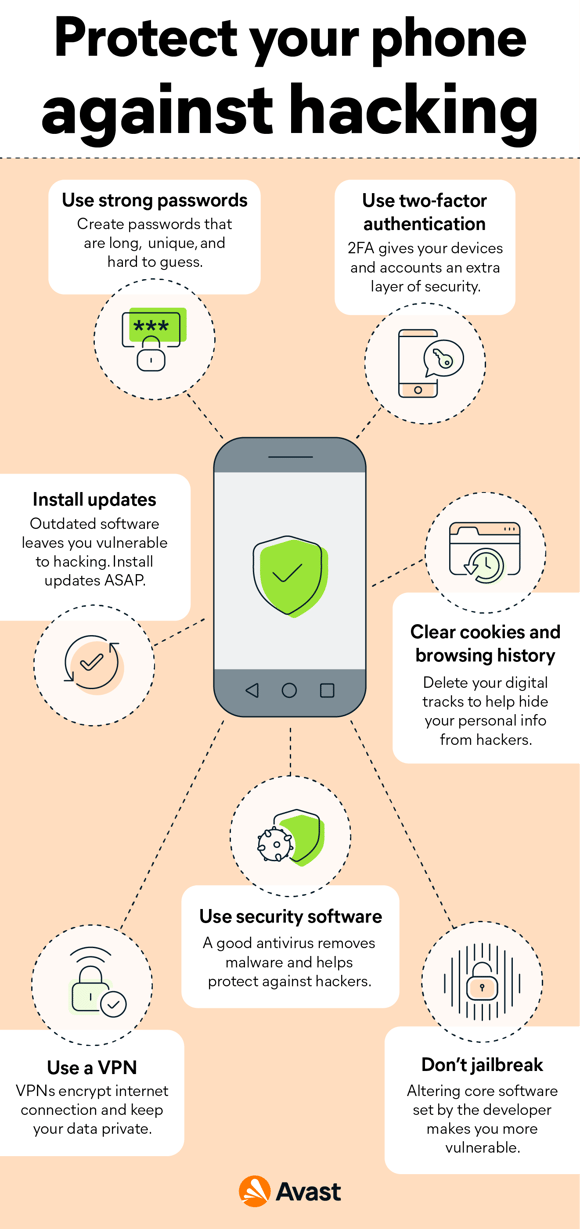
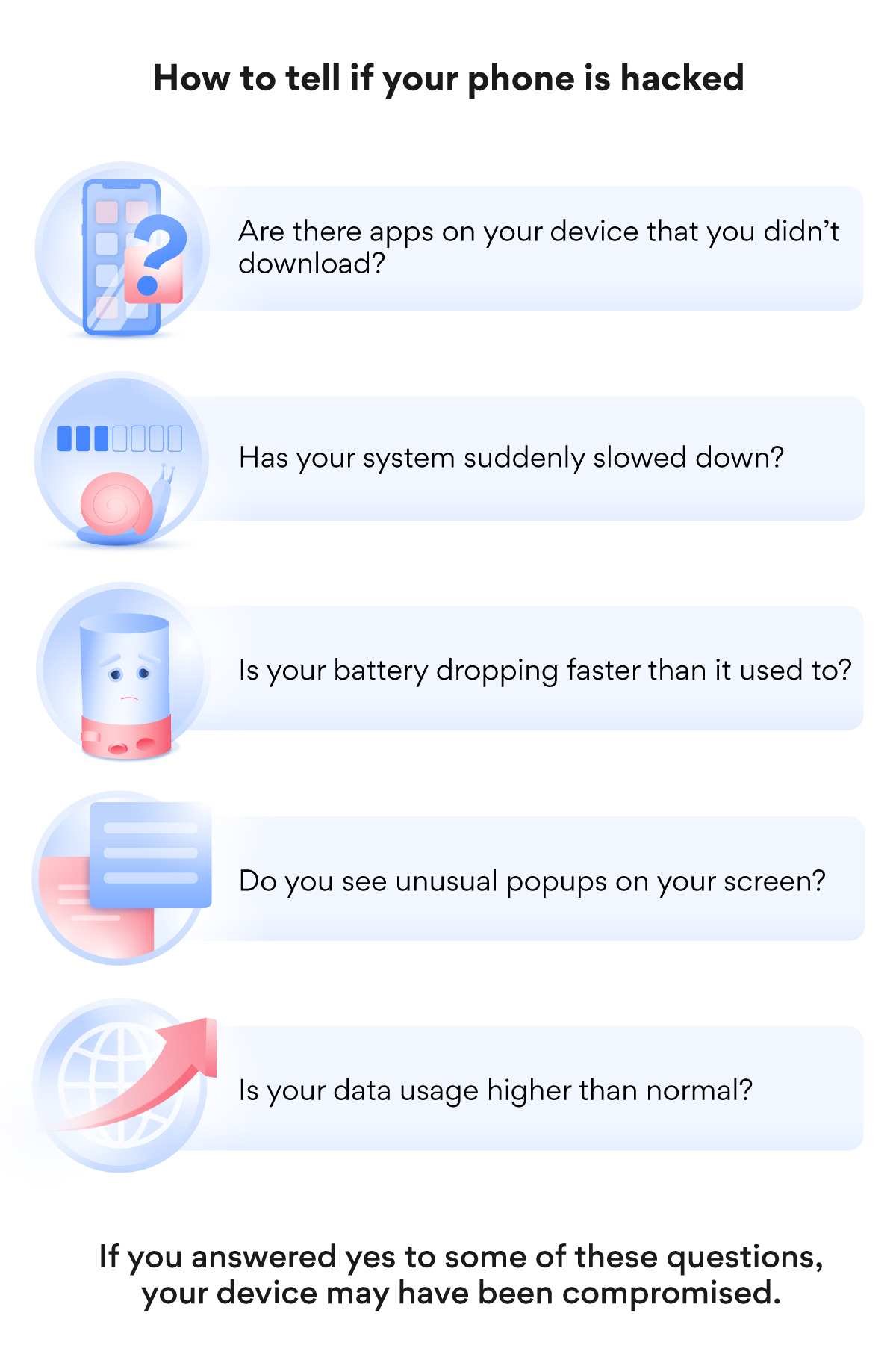
A phone’s battery draining too quickly can be a sign that there’s something going on in the background.
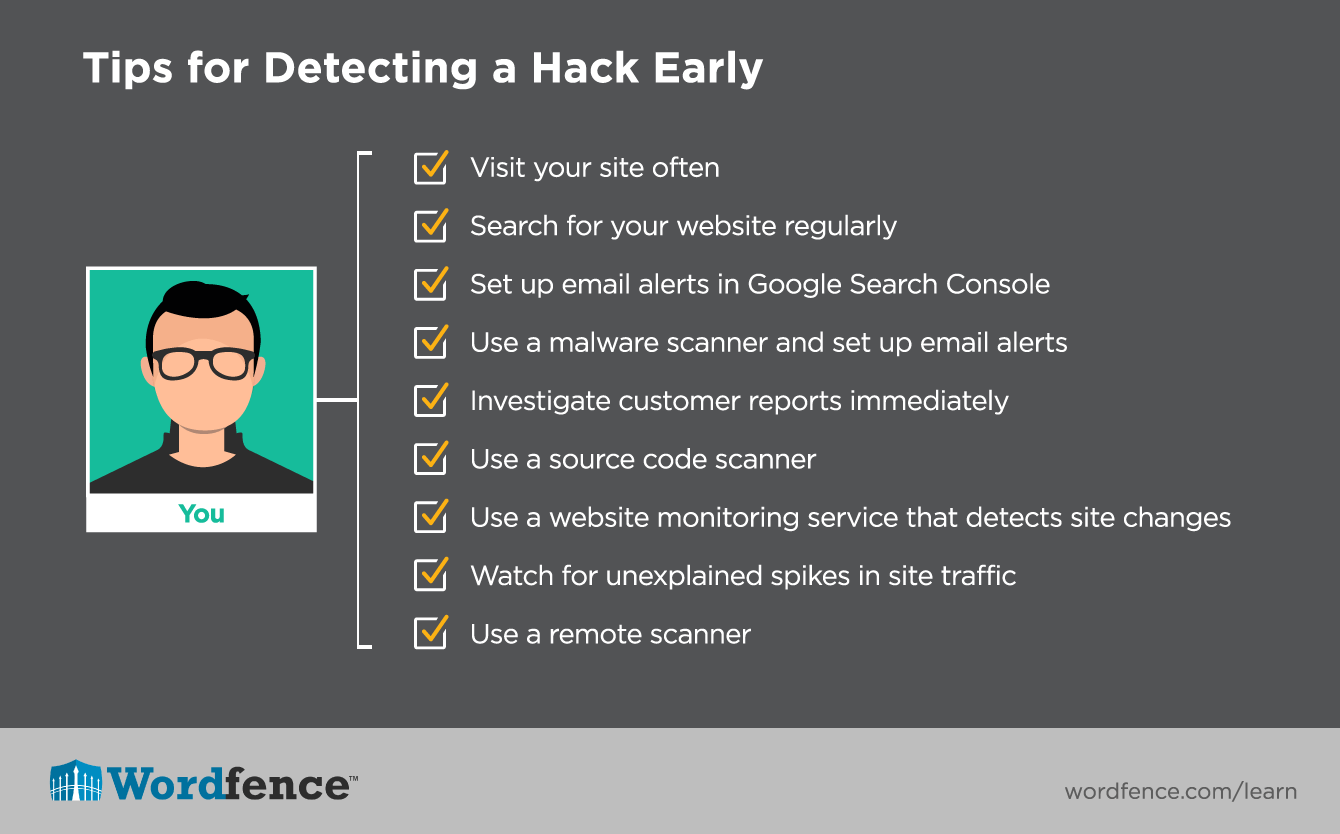
How to detect hacking. How to detect hackers on your network: Install a intrusion detection system (ids) to know if the system has been hacked first thing to do after suspicion of a hacker attack is to setup an ids (intrusion detection system) to detect. This video is the updated version of how to check easily if you have been hacked or not, this is not some reliable method, its just a way to check it quickly.
5 ways to check if your android device is hacked 1. By using various encoding techniques like ascii encoding, hexadecimal encoding, etc. Installation of some strange applications automatically can be one of the main signs of hacking your phone because hackers may have.
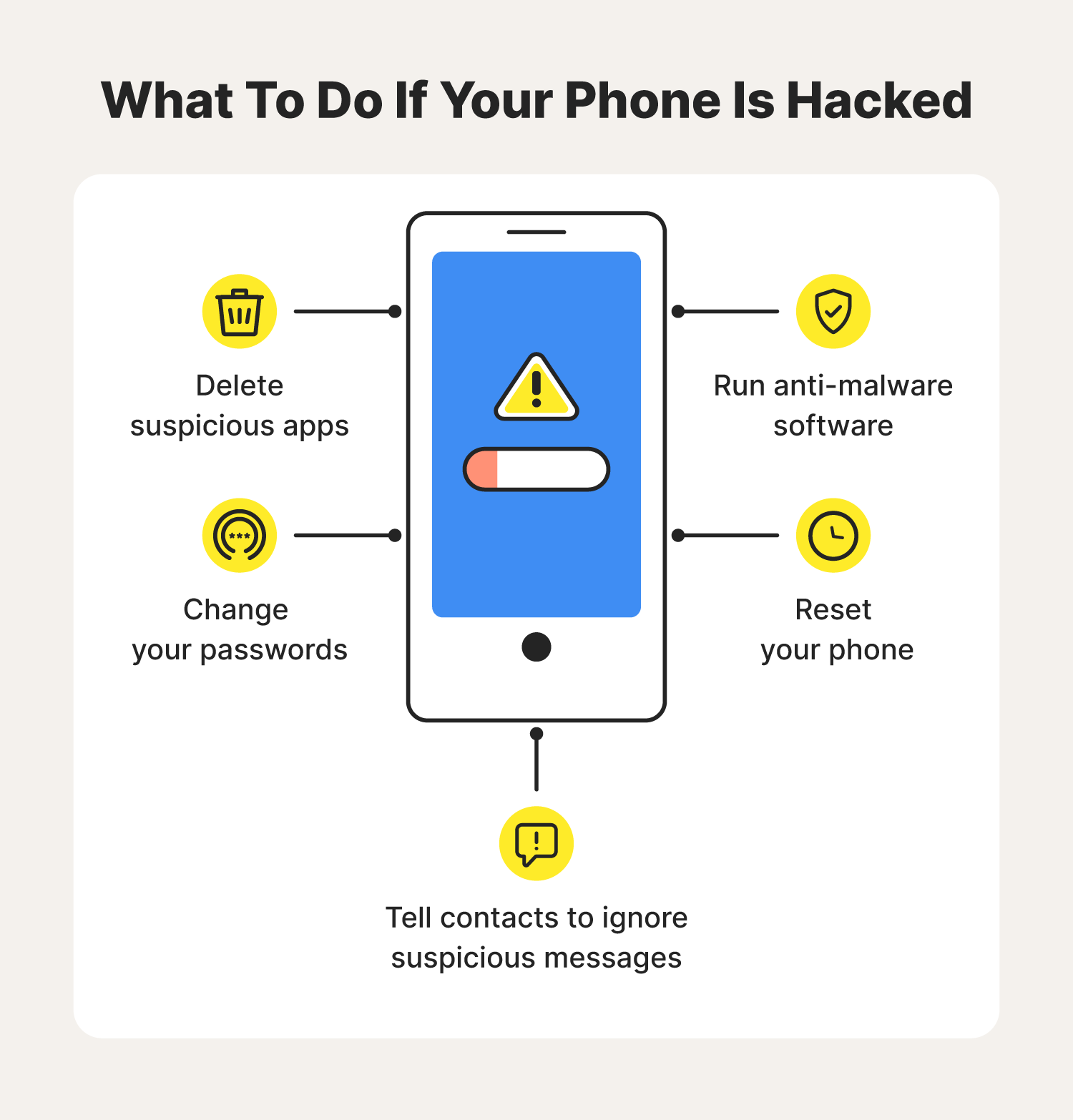
Close the browser window where the “warning” appeared. Encrypted text cannot be recognised by ids. This could just mean that there’s a setting you need to change, or it could mean.
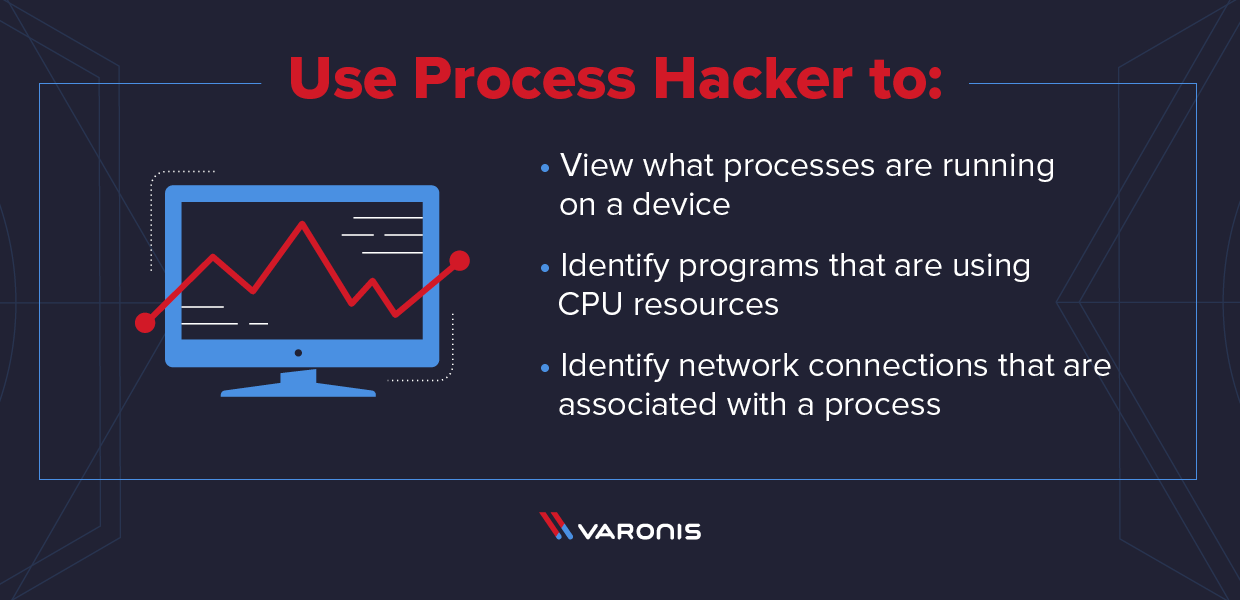
Even if you don't see clear signs of suspicious activity, something. To find a hacker that may be connected to your computer, run tcpview and accept the license agreement. A world of adventure awaits.
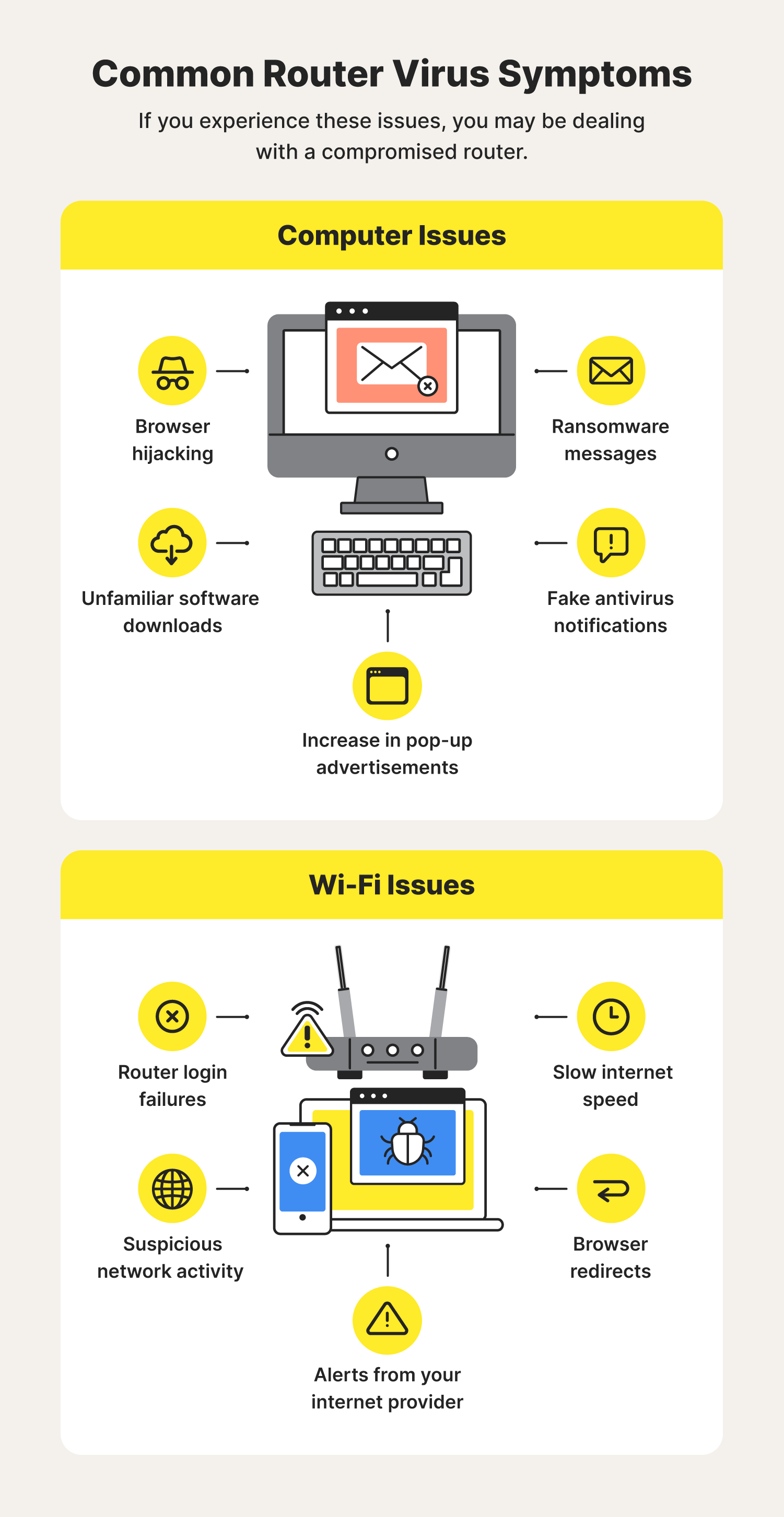
Lateral movement refers to a group of methods cyber criminals use to explore an infected network to find vulnerabilities, escalate access privileges, and reach their ultimate target. Poor battery life or extreme battery usage. Then, make sure you are using the latest version of your browser.
New programs have been installed when accepted procedures exist regarding new software installation, one telltale. Five command line tools to detect windows hacks. You can find a hacker at any moment.